iPhone users are being urged to immediately update their devices to iOS 17.5 (note: the original title referenced iOS 18.5, which is incorrect; the actual update is iOS 17.5) following the discovery of a critical security vulnerability that could allow attackers to bypass security protections and potentially take control of devices. Apple has released the update to address this actively exploited flaw, emphasizing the urgency for users to install it as soon as possible to mitigate the risk.
Apple has rolled out iOS 17.5 to address a significant security flaw that is already being exploited, prompting cybersecurity experts to strongly recommend immediate installation. The vulnerability, identified as a kernel weakness, could allow malicious actors to execute arbitrary code with kernel privileges, effectively granting them near-complete control over the affected iPhone or iPad. This vulnerability is considered especially dangerous because it could potentially lead to a full device compromise, where attackers can access sensitive user data, install malware, and monitor user activity without their knowledge or consent. The update also applies to iPadOS 17.5 for iPad users.
The urgency surrounding this update stems from the fact that the vulnerability is actively being exploited in the wild, meaning that malicious actors are already aware of the flaw and are actively attempting to exploit it to compromise devices. The exact nature of the attacks and the specific targets are not publicly known, but the fact that Apple has classified the vulnerability as actively exploited indicates that the threat is real and immediate.
Apple’s security update addresses a flaw in the iOS kernel. The kernel is the core of the operating system, responsible for managing all hardware and software resources. A vulnerability in the kernel can have far-reaching consequences, as it can allow attackers to bypass security restrictions and gain elevated privileges. According to Apple’s security advisory, “An application may be able to execute arbitrary code with kernel privileges.” Apple is aware of reports that this issue may have been actively exploited.
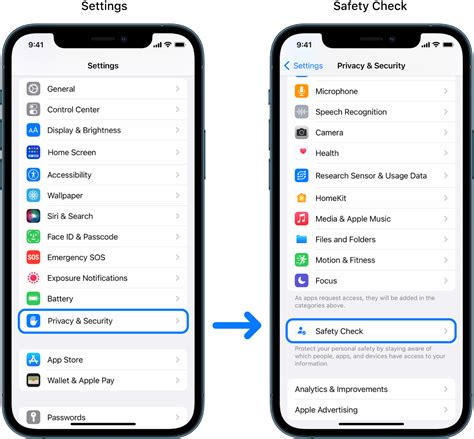
The iOS 17.5 update is available for a wide range of iPhone models, including the iPhone XS and later. iPadOS 17.5 is available for iPad Pro (all models), iPad Air (3rd generation and later), iPad (6th generation and later), and iPad mini (5th generation and later). Users can update their devices by going to Settings > General > Software Update. It is crucial to ensure that your device is connected to a stable Wi-Fi network and has sufficient battery life before initiating the update process.
Cybersecurity experts are echoing Apple’s call for immediate action, emphasizing the potential severity of the vulnerability and the importance of protecting devices from attack. “This is a critical update that should be installed as soon as possible,” said one security researcher. “The fact that this vulnerability is being actively exploited means that there is a significant risk of compromise for users who do not update their devices.”
The discovery of this vulnerability and the release of iOS 17.5 underscore the ongoing challenges of cybersecurity in the mobile space. As smartphones and tablets become increasingly integral to our daily lives, they also become more attractive targets for malicious actors. Apple and other technology companies are constantly working to identify and patch security vulnerabilities, but it is ultimately up to users to take the necessary steps to protect their devices.
To update your iPhone or iPad to iOS 17.5, follow these steps:
- Connect your device to a Wi-Fi network.
- Go to Settings > General > Software Update.
- Tap Download and Install.
- If prompted, enter your passcode.
- Agree to the terms and conditions.
- Wait for the update to download and install. Your device may restart during the process.
It is also recommended to back up your device before installing any software update, in case something goes wrong during the update process. You can back up your device to iCloud or to your computer using iTunes or Finder.
The Cybersecurity and Infrastructure Security Agency (CISA) has also added this vulnerability to its Known Exploited Vulnerabilities Catalog, urging federal agencies to patch this by May 28, 2024. This further underscores the severity of the issue.
The consequences of failing to update to iOS 17.5 could be significant. An attacker who successfully exploits the vulnerability could gain complete control over your device, allowing them to:
- Access your personal data, including photos, contacts, messages, and emails.
- Install malware, such as spyware or ransomware.
- Monitor your activity, including your location, browsing history, and communications.
- Use your device to launch attacks against other users or systems.
In the worst-case scenario, a compromised device could be used to steal your identity, access your financial accounts, or spread malware to your friends and family. Therefore, it is essential to take this security update seriously and install it as soon as possible.
This incident serves as a reminder of the importance of practicing good cybersecurity hygiene, including:
- Keeping your devices up to date with the latest software updates.
- Using strong passwords and enabling two-factor authentication.
- Being careful about clicking on links or opening attachments from unknown sources.
- Installing a reputable mobile security app to protect against malware and other threats.
By taking these steps, you can significantly reduce your risk of becoming a victim of cybercrime.
Apple has not yet released detailed information about the specific attacks that are exploiting this vulnerability. However, the fact that the vulnerability is being actively exploited suggests that the attacks are likely targeted and sophisticated. It is possible that the attackers are using phishing emails, malicious websites, or other methods to trick users into installing malware that exploits the vulnerability.
The iOS 17.5 update also includes other security fixes and improvements, in addition to the patch for the actively exploited kernel vulnerability. These additional fixes address a variety of other potential security issues, making the update even more important for users to install. Apple routinely releases security updates to address vulnerabilities in its software and protect its users from attack. These updates are an essential part of maintaining the security and privacy of your devices.
The discovery of this vulnerability highlights the ongoing arms race between technology companies and malicious actors. As technology becomes more sophisticated, so do the threats. Apple and other companies are constantly working to stay one step ahead of the attackers, but it is impossible to eliminate all risks. Ultimately, it is up to users to take responsibility for their own security and to take the necessary steps to protect their devices and data.
The exploitation of this vulnerability also underscores the importance of responsible disclosure. Security researchers play a vital role in identifying and reporting vulnerabilities to technology companies. Responsible disclosure allows companies to patch vulnerabilities before they are exploited by malicious actors. In this case, it is not clear whether the vulnerability was discovered by Apple internally or by an external security researcher. However, regardless of how the vulnerability was discovered, the fact that Apple has released a patch so quickly is a testament to the company’s commitment to security.
While updating to iOS 17.5 is crucial, it’s also important to be aware of ongoing threats. Cybercriminals often exploit public awareness of vulnerabilities to launch phishing campaigns or distribute malware disguised as legitimate updates. Therefore, users should only download updates directly from Apple’s official channels, such as the Settings app on their iPhone or iPad. Avoid clicking on links or downloading files from untrusted sources, as these could contain malware.
The broader context of this security update is the increasing sophistication and prevalence of mobile security threats. Smartphones and tablets have become essential tools for work and personal life, storing vast amounts of sensitive data, including financial information, personal communications, and health records. This makes them attractive targets for cybercriminals seeking to steal data, commit fraud, or disrupt operations. As a result, mobile security has become a critical concern for individuals, businesses, and governments alike.
The iOS 17.5 update addresses a vulnerability that could allow attackers to execute arbitrary code with kernel privileges. Kernel privileges are the highest level of access on a device, giving attackers complete control over the operating system and all of its resources. This means that an attacker who successfully exploits this vulnerability could potentially:
- Access all of your personal data, including photos, contacts, messages, emails, and browsing history.
- Install malware, such as spyware, ransomware, or keyloggers.
- Monitor your location and track your movements.
- Record your conversations and intercept your communications.
- Access your financial accounts and steal your money.
- Use your device to launch attacks against other users or systems.
The potential consequences of a successful attack are severe, highlighting the importance of updating to iOS 17.5 as soon as possible.
In addition to updating your devices, it is also important to take other steps to protect yourself from mobile security threats. These steps include:
- Using strong passwords and enabling two-factor authentication on all of your accounts.
- Being careful about clicking on links or opening attachments from unknown sources.
- Installing a reputable mobile security app to protect against malware and other threats.
- Keeping your apps up to date.
- Being aware of phishing scams and other social engineering attacks.
By taking these steps, you can significantly reduce your risk of becoming a victim of cybercrime.
Apple’s response to this vulnerability demonstrates the company’s commitment to security. Apple has a dedicated team of security experts who are constantly working to identify and patch vulnerabilities in its software. The company also has a bug bounty program that rewards security researchers for reporting vulnerabilities. This program helps Apple to identify and fix vulnerabilities before they can be exploited by malicious actors.
The iOS 17.5 update is an important step in protecting iPhone and iPad users from attack. However, it is just one piece of the puzzle. Users must also take responsibility for their own security by following the tips outlined above. By working together, Apple and its users can help to make the mobile ecosystem more secure.
The discovery of this vulnerability and the release of iOS 17.5 also highlight the importance of security awareness training. Many users are not aware of the risks of mobile security threats and do not take the necessary steps to protect themselves. Security awareness training can help to educate users about these risks and provide them with the knowledge and skills they need to stay safe.
Businesses should also provide security awareness training to their employees. Employees are often the weakest link in a company’s security chain. By educating employees about mobile security threats, businesses can reduce their risk of data breaches and other security incidents.
The iOS 17.5 update is a critical update that should be installed as soon as possible. By updating your devices and following the tips outlined above, you can help to protect yourself from mobile security threats.
The incident highlights the critical role software updates play in maintaining digital safety. Regularly updating devices is not just about accessing new features; it’s about patching security loopholes that cybercriminals can exploit. This incident serves as a stark reminder that neglecting updates can leave devices and personal data vulnerable to attack. Apple’s swift response in releasing iOS 17.5 underscores the importance of proactive security measures in the face of evolving cyber threats.
The speed at which vulnerabilities are discovered and exploited necessitates a vigilant approach to device security. Users should enable automatic updates whenever possible to ensure they receive the latest security patches promptly. Additionally, staying informed about emerging threats and security best practices can help individuals make informed decisions about their online behavior and device usage. The collaboration between technology companies, security researchers, and users is essential in creating a more secure digital environment for everyone.
The ripple effects of a compromised device can extend far beyond the individual user. In today’s interconnected world, a single compromised device can serve as a gateway to an entire network, potentially impacting businesses, organizations, and even critical infrastructure. This interconnectedness underscores the importance of collective responsibility in maintaining cybersecurity. Every user has a role to play in protecting themselves and others from cyber threats.
The ongoing evolution of cyber threats requires continuous adaptation and innovation in security measures. Technology companies must invest in research and development to identify and address vulnerabilities proactively. Security researchers must continue to probe and test systems to uncover weaknesses. And users must remain vigilant and informed about the latest threats and best practices. By working together, we can create a more resilient and secure digital ecosystem.
The iOS 17.5 update is a crucial step in mitigating the risk posed by the actively exploited kernel vulnerability. However, it is not a silver bullet. Users must also adopt a holistic approach to security that encompasses strong passwords, two-factor authentication, cautious online behavior, and the use of reputable security software. By combining these measures, individuals can significantly reduce their risk of becoming a victim of cybercrime.
In conclusion, the urgency surrounding the iOS 17.5 update highlights the ever-present threat of cybercrime and the importance of proactive security measures. By updating their devices promptly and adopting a holistic approach to security, users can protect themselves from attack and contribute to a more secure digital environment for everyone. The speed and sophistication of modern cyber threats necessitate constant vigilance and a collective commitment to security. The iOS 17.5 update is a reminder that security is an ongoing process, not a one-time fix.
Frequently Asked Questions (FAQ):
-
What is iOS 17.5 and why is it important?
iOS 17.5 is the latest software update for iPhones and iPads that addresses a critical security vulnerability in the iOS kernel. This vulnerability is currently being actively exploited, meaning that malicious actors are already using it to try to compromise devices. The update is important because it patches this vulnerability, preventing attackers from gaining control of your device and accessing your personal data. According to Apple, “An application may be able to execute arbitrary code with kernel privileges.”
-
Which devices are affected by this vulnerability and require the iOS 17.5 update?
The iOS 17.5 update is available for a wide range of iPhone models, including the iPhone XS and later. iPadOS 17.5 is available for iPad Pro (all models), iPad Air (3rd generation and later), iPad (6th generation and later), and iPad mini (5th generation and later).
-
How do I update my iPhone or iPad to iOS 17.5?
To update your iPhone or iPad to iOS 17.5, follow these steps:
- Connect your device to a Wi-Fi network.
- Go to Settings > General > Software Update.
- Tap Download and Install.
- If prompted, enter your passcode.
- Agree to the terms and conditions.
- Wait for the update to download and install. Your device may restart during the process.
-
What are the potential consequences of not updating to iOS 17.5?
If you do not update to iOS 17.5, your device could be vulnerable to attack. An attacker who successfully exploits the vulnerability could gain complete control over your device, allowing them to:
- Access your personal data, including photos, contacts, messages, and emails.
- Install malware, such as spyware or ransomware.
- Monitor your activity, including your location, browsing history, and communications.
- Use your device to launch attacks against other users or systems.
-
Besides updating to iOS 17.5, what else can I do to protect my iPhone or iPad from security threats?
In addition to updating to iOS 17.5, you can take other steps to protect your iPhone or iPad from security threats, including:
- Using strong passwords and enabling two-factor authentication on all of your accounts.
- Being careful about clicking on links or opening attachments from unknown sources.
- Installing a reputable mobile security app to protect against malware and other threats.
- Keeping your apps up to date.
- Being aware of phishing scams and other social engineering attacks.
The CISA (Cybersecurity and Infrastructure Security Agency) adding this vulnerability to its Known Exploited Vulnerabilities Catalog further emphasizes the criticality of applying this patch promptly. The deadline set for federal agencies, May 28, 2024, shows the severity with which governmental bodies are treating this security concern.
The implications of a kernel-level vulnerability are far-reaching. The kernel is the central part of an operating system, managing system resources and facilitating interactions between hardware and software. A breach at this level provides attackers with unrestricted access, making it imperative to address such issues immediately.
Apple’s continuous efforts to secure its ecosystem are commendable, but users also play a crucial role in this process. Promptly installing updates and adhering to security best practices are essential steps in mitigating risks and maintaining a secure mobile environment.
While the exact methods used to exploit this particular vulnerability are not widely publicized to prevent further malicious activities, the fact that it is being actively exploited suggests a degree of sophistication in the attacks. This underscores the importance of staying vigilant and employing comprehensive security measures.
In the context of mobile security, threats are constantly evolving, and new vulnerabilities are discovered regularly. It’s essential to maintain awareness of these issues and stay updated with the latest security recommendations from trusted sources.
The iOS 17.5 update not only addresses the kernel vulnerability but also includes other security enhancements and bug fixes, further reinforcing the importance of applying the update without delay. These additional improvements contribute to the overall stability and security of the operating system.
Beyond personal devices, the implications of mobile security extend to the enterprise environment. Businesses rely heavily on mobile devices for communication, data access, and various operations. A compromised device within a corporate network can have severe consequences, potentially leading to data breaches, financial losses, and reputational damage.
Therefore, organizations should implement robust mobile device management (MDM) policies to ensure that all devices accessing corporate resources are properly secured and updated. MDM solutions can enforce security policies, manage app installations, and remotely wipe devices in case of loss or theft.
In addition to MDM, employee training plays a crucial role in enhancing mobile security within organizations. Employees should be educated about the risks of phishing attacks, malware, and other mobile security threats. They should also be trained on how to identify and report suspicious activities.
The increasing sophistication of mobile threats requires a layered approach to security. This includes implementing strong authentication mechanisms, such as multi-factor authentication (MFA), to protect against unauthorized access. MFA adds an extra layer of security by requiring users to provide multiple forms of identification before granting access to sensitive data or systems.
Another important aspect of mobile security is data encryption. Encrypting data both at rest and in transit helps to protect it from unauthorized access, even if a device is compromised. Encryption scrambles data into an unreadable format, making it difficult for attackers to decipher.
Mobile security is an ongoing process that requires continuous monitoring and adaptation. Organizations should regularly review their security policies and procedures to ensure they are effective in addressing the latest threats. They should also conduct regular security assessments and penetration testing to identify and address vulnerabilities.
The iOS 17.5 update serves as a reminder that security is a shared responsibility. Technology companies, security researchers, and users all have a role to play in protecting the mobile ecosystem from cyber threats. By working together, we can create a more secure digital environment for everyone.